
Are cybercrimes really something we need to be concerned about in the networking and cloud industries? That’s a great question and I’m glad you asked! Adversaries are becoming more aggressive and creative every day as they continue to probe for valuable information from US companies. The FBI estimates that US companies lose as much as $600 BILLION annually to IP and technology theft. Much of that loss is due to Insider Threats, but as US companies continue to focus on preventing Insiders, the adversaries are becoming more aggressive with phishing and other cyber activities. Take a look at some interesting statistics noted in the FBI’s 2018 Internet Crimes Report:
We take these threats very serious at Extreme. We understand that as a US Federal contractor, we have an even higher risk of compromise from the aforementioned adversaries. We maintain direct contact with our local FBI field offices, as well as with Cybersecurity Officers at the Defense Counterintelligence and Security Agency. These relationships allow our security experts to receive current information regarding cybersecurity threats and implement preventative measures to reduce our risk. We also use these relationships to help us design and deploy an aggressive security program, which includes awareness and education, reporting, simulation tests, and other similar preventative measures. For this blog, I’d like to focus our attention on phishing, as it is the primary method used to illegally solicit sensitive information.
You can delve down to the micro-level and define dozens of types of phishing, but at the end of the day, there are three basic categories:
Deceptive Phishing: The most common type of phishing has the adversary impersonating a legitimate person or company. They use this technique to elicit sensitive information or steal login credentials. They will frequently use threatening language that requires swift action from the recipient to have them act before thinking. General deceptive phishing typically doesn’t target specific individuals.
Spear Phishing: Spear phishing is a form of deceptive phishing that includes a personal element. In these cases, the adversary will include the target’s name, phone number and other personal information in order to trick the target into believing they have some type of legitimate connection with the sender. This method is very common on social media sites where it is easy for an adversary to create a fake profile to appear to be in a similar role or industry as the target.
Whaling: Whaling is another form of spear-phishing with the specific goal of targeting senior executives of an organization. The assumption here is that adversaries are targeting executives because they typically have access to more sensitive information and have financial authority. Some cases have resulted in the adversary obtaining an executive’s credentials and using them to have money illegally transferred to the adversary’s offshore account.
Phishing emails are normally designed to appear they are coming from a trusted source. They may appear to be from a partner company, customer, bank, university, the government, or any other source you commonly communicate with. In most cases, they bait you in by convincing you there may be an issue or a need.
The following are some signs of a scam:
Let’s pretend you get an email from what appears to be a legitimate credit card company, regarding your corporate account. The sending email appears to be legit and it contains the following image:
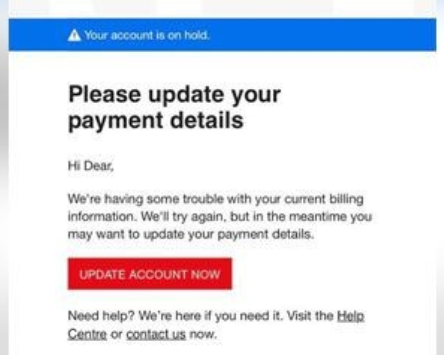
Did you recognize the signs that it’s a scam from the list above?
This is one of the most common, and successful, methods used to convince a user to click on a malicious link. The adversary takes very meticulous measures to appear to be legitimate. They use a company logo, an email address with the company name, and common issues that may arise with that type of account.
In any case where you receive an email, text or other correspondence requesting information or that you click on a link, verify the legitimacy of the request using other means prior to taking any action with the solicitation. Unfortunately, IT can’t filter out every potentially malicious email. It’s up to users to be able to recognize the warning signs and report such activity.
Recognizing phishing attempts is the first step in protecting yourself, Extreme, and our customers. Once you recognize an attempt, it’s very important that you report the information so that we can take steps to further protect against these types of attacks. We work closely with our partners, customers, and government security agencies in order to thwart these efforts before they get to your inbox or mobile device. It takes a collaborative effort for us to be successful, and that starts with your reporting efforts.
There are several ways for you to report phishing. For instance, most professional email software includes a tool where you can simply click on “Report Phishing” on the toolbar.
If for some reason that doesn’t work, or the solicitation comes from a different source other than email, you can simply email your security or IT team to report the activity. Whatever mechanism you choose to use for reporting, it’s imperative that you do so swiftly in order to thwart any similar efforts occurring at your organization.
In addition to reporting phishing, you and your organization can take several measures to prevent your adversaries from successfully probing sensitive information.
Invest in detection tools: There are several tools you can install on your network that will screen for this activity behind the scenes. Like antivirus software, these tools are regularly updated with “known threats” that are pushed out on a recurring basis. While not and end-all solution, the better versions of these tools will filter out most of the known threats that are lurking.
Run simulation tests: Simulation tests have proven to be extremely successful in improving user awareness at my places of employment. These tests allow you to identify how successful your education program is and the frequency at which employees are reporting phishing activity. There are tools available that will provide you specific metrics on your simulation. These include:
These metrics are extremely valuable in assessing the effectiveness of security education at your organization. This data allows you to increase your security awareness across the organization, and even focus on certain departments that may have struggled with the simulation more so than others.
Education: Educating your staff will always prove to be the most effective measure you can take in combatting phishing attempts. If an employee doesn’t know how to recognize phishing, they surely will not notice the signs. If an employee doesn’t know how to report phishing, it’s unlikely they will do so. It’s up to the security professionals at your organization to ensure the staff is aware of this growing threat, that they know how to identify potential phishing attempts, and that they know how to report the activity.
Whether you’re in manufacturing, integration or services, rest assured someone is trying to gain access to your systems and sensitive information. We all have an obligation to take the necessary measures to protect the organizations we work for. Those of us working as federal contractors have an even great obligation; failure on our part potentially places national security at risk. The stakes are high and taking a little extra time to screen emails and report those that are suspicious will go a long way in minimizing the success of our adversaries.